Leveraging GitHub Actions Environment Secrets and Variables in Your Deployment Workflows
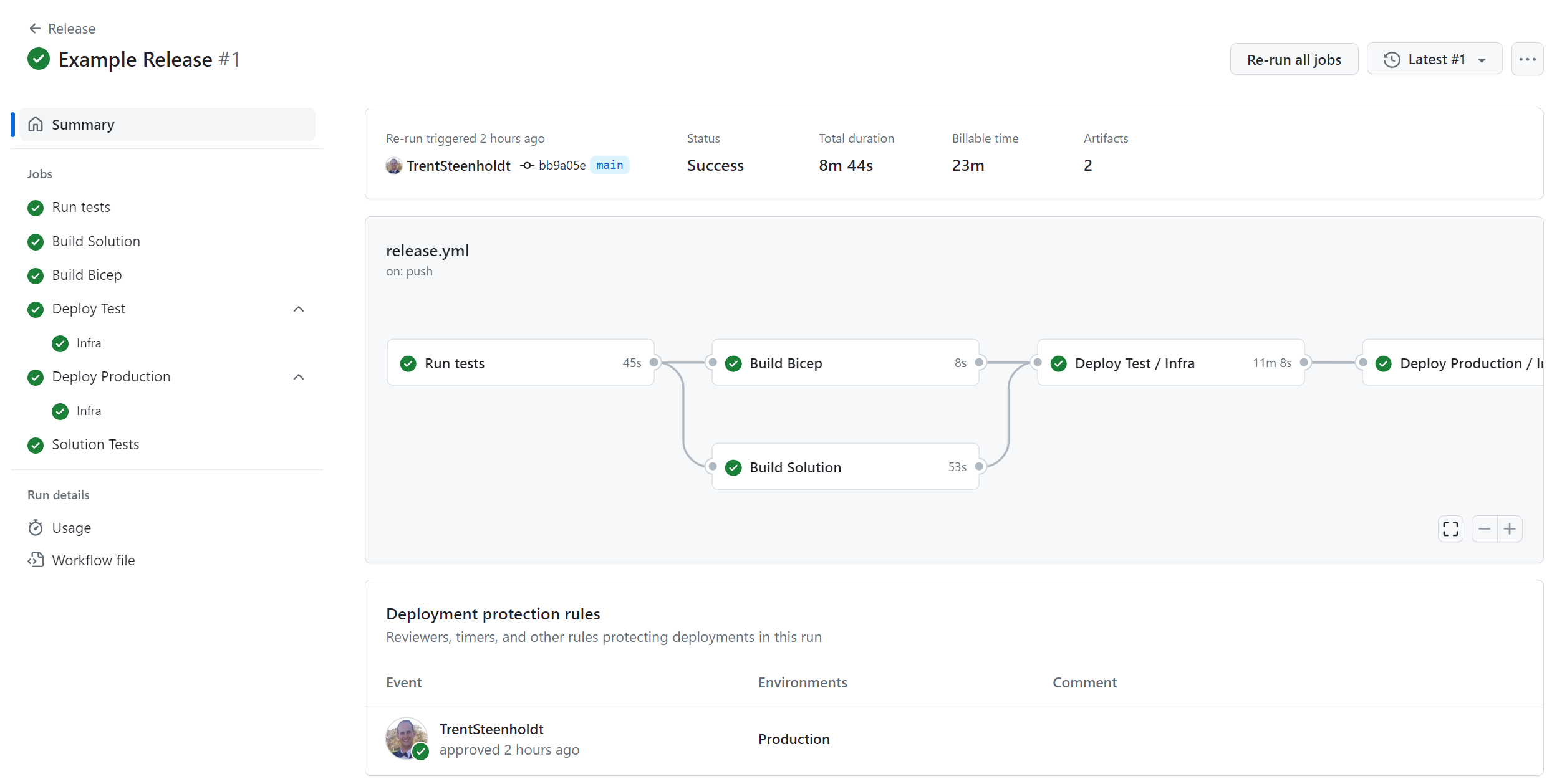
GitHub Actions Environments are powerful in managing deployment workflows, but their documentation doesn't always provide clear guidance on handling secrets and variables. In this summary blog post, we discuss the various ways to leverage Environment secrets and variables, discussing their benefits and limitations in different scenarios.
Summary of lessons learned
- Matrices are not suitable for managing environment variables, secrets, and controls. They're better suited for handling different versions of your app or code.
- Splitting YAML files into workflow callers and using environments can become complicated when accessing secrets and variables.
- Passing secrets as inputs to workflow callers is the only way to use GitHub Action Environment secrets and variables in this scenario. However, the user experience in the GitHub Actions UI is left somewhat limiting.
- Using workflow callers over custom Actions provides flexibility and simplicity when dealing with complex Infrastructure as Code (IaC) deployment scenarios.
Conclusion
When using workflow callers, there's no perfect solution for handling environment secrets and variables in YAML files. While using GitHub Actions Environments can streamline deployment workflows, the logical way of handling secrets and variables can be more complex than desired. Ultimately, the choice between the different methods will depend on your preferences.
Check out the full deep-dive blog post for the working examples discussed in this summary.

